Approved of 212-89 study guide materials and training materials for EC-Council certification for client, Real Success Guaranteed with Updated 212-89 pdf dumps vce Materials. 100% PASS EC Council Certified Incident Handler (ECIH v2) exam Today!
Free 212-89 Demo Online For EC-Council Certifitcation:
NEW QUESTION 1
The policy that defines which set of events needs to be logged in order to capture and review the important data in a timely manner is known as:
- A. Audit trail policy
- B. Logging policy
- C. Documentation policy
- D. Evidence Collection policyAn information security policy must be:
- E. Distributed and communicated
- F. Enforceable and Regularly updated
- G. Written in simple language
- H. All the above
Answer: D
NEW QUESTION 2
To whom should an information security incident be reported?
- A. It should not be reported at all and it is better to resolve it internally
- B. Human resources and Legal Department
- C. It should be reported according to the incident reporting & handling policy
- D. Chief Information Security Officer
Answer: C
NEW QUESTION 3
An incident recovery plan is a statement of actions that should be taken before, during or after an incident. Identify which of the following is NOT an objective of the incident recovery plan?
- A. Creating new business processes to maintain profitability after incident
- B. Providing a standard for testing the recovery plan
- C. Avoiding the legal liabilities arising due to incident
- D. Providing assurance that systems are reliable
Answer: A
NEW QUESTION 4
Which of the following service(s) is provided by the CSIRT:
- A. Vulnerability handling
- B. Technology watch
- C. Development of security tools
- D. All the above
Answer: D
NEW QUESTION 5
Which of the following terms may be defined as “a measure of possible inability to achieve a goal, objective, or target within a defined security, cost plan and technical limitations that adversely affects the organization’s operation and revenues?
- A. Risk
- B. Vulnerability
- C. Threat
- D. Incident Response
Answer: A
NEW QUESTION 6
A computer virus hoax is a message warning the recipient of non-existent computer virus. The message is usually a chain e-mail that tells the recipient to forward it to every one they know. Which of the following is NOT a symptom of virus hoax message?
- A. The message prompts the end user to forward it to his / her e-mail contact list and gain monetary benefits in doing so
- B. The message from a known email id is caught by SPAM filters due to change of filter settings
- C. The message warns to delete certain files if the user does not take appropriate action
- D. The message prompts the user to install Anti-Virus
Answer: A
NEW QUESTION 7
Which one of the following is the correct sequence of flow of the stages in an incident response:
- A. Containment - Identification - Preparation - Recovery - Follow-up - Eradication
- B. Preparation - Identification - Containment - Eradication - Recovery - Follow-up
- C. Eradication - Containment - Identification - Preparation - Recovery - Follow-up
- D. Identification - Preparation - Containment - Recovery - Follow-up - Eradication
Answer: B
NEW QUESTION 8
Electronic evidence may reside in the following:
- A. Data Files
- B. Backup tapes
- C. Other media sources
- D. All the above
Answer: D
NEW QUESTION 9
Spyware tool used to record malicious user’s computer activities and keyboard stokes is called:
- A. adware
- B. Keylogger
- C. Rootkit
- D. Firewall
Answer: B
NEW QUESTION 10
Quantitative risk is the numerical determination of the probability of an adverse event and the extent of the losses due to the event. Quantitative risk is calculated as:
- A. (Probability of Loss) X (Loss)
- B. (Loss) / (Probability of Loss)
- C. (Probability of Loss) / (Loss)
- D. Significant Risks X Probability of Loss X Loss
Answer: A
NEW QUESTION 11
The flow chart gives a view of different roles played by the different personnel of CSIRT. Identify the incident response personnel denoted by A, B, C, D, E, F and G.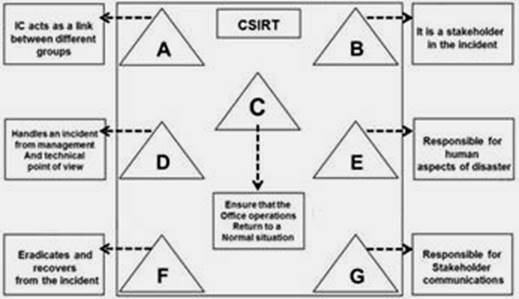
- A. A-Incident Analyst, B- Incident Coordinator, C- Public Relations, D-Administrator, E- Human Resource, FConstituency, G-Incident Manager
- B. A- Incident Coordinator, B-Incident Analyst, C- Public Relations, D-Administrator, E- Human Resource, FConstituency, G-Incident Manager
- C. A- Incident Coordinator, B- Constituency, C-Administrator, D-Incident Manager, E- Human Resource, FIncident Analyst, G-Public relations
- D. A- Incident Manager, B-Incident Analyst, C- Public Relations, D-Administrator, E- Human Resource, FConstituency, G-Incident Coordinator
Answer: C
NEW QUESTION 12
Business Continuity provides a planning methodology that allows continuity in business operations:
- A. Before and after a disaster
- B. Before a disaster
- C. Before, during and after a disaster
- D. During and after a disaster
Answer: C
NEW QUESTION 13
_____ record(s) user’s typing.
- A. Spyware
- B. adware
- C. Virus
- D. Malware
Answer: A
NEW QUESTION 14
The very well-known free open source port, OS and service scanner and network discovery utility is called:
- A. Wireshark
- B. Nmap (Network Mapper)
- C. Snort
- D. SAINT
Answer: B
NEW QUESTION 15
The insider risk matrix consists of technical literacy and business process knowledge vectors. Considering the matrix, one can conclude that:
- A. If the insider’s technical literacy is low and process knowledge is high, the risk posed by the threat will be insignificant.
- B. If the insider’s technical literacy and process knowledge are high, the risk posed by the threat will be insignificant.
- C. If the insider’s technical literacy is high and process knowledge is low, the risk posed by the threat will be high.
- D. If the insider’s technical literacy and process knowledge are high, the risk posed by the threat will be high.
Answer: D
NEW QUESTION 16
Removing or eliminating the root cause of the incident is called:
- A. Incident Eradication
- B. Incident Protection
- C. Incident Containment
- D. Incident Classification
Answer: A
NEW QUESTION 17
An audit trail policy collects all audit trails such as series of records of computer events, about an operating system, application or user activities. Which of the following statements is NOT true for an audit trail policy:
- A. It helps calculating intangible losses to the organization due to incident
- B. It helps tracking individual actions and allows users to be personally accountable for their actions
- C. It helps in compliance to various regulatory laws, rules,and guidelines
- D. It helps in reconstructing the events after a problem has occurred
Answer: A
NEW QUESTION 18
An access control policy authorized a group of users to perform a set of actions on a set of resources. Access to resources is based on necessity and if a particular job role requires the use of those resources. Which of the following is NOT a fundamental element of access control policy
- A. Action group: group of actions performed by the users on resources
- B. Development group: group of persons who develop the policy
- C. Resource group: resources controlled by the policy
- D. Access group: group of users to which the policy applies
Answer: B
NEW QUESTION 19
Identify the malicious program that is masked as a genuine harmless program and gives the attacker unrestricted access to the user’s information and system. These programs may unleash dangerous programs that may erase the unsuspecting user’s disk and send the victim’s credit card numbers and passwords to a stranger.
- A. Cookie tracker
- B. Worm
- C. Trojan
- D. Virus
Answer: C
NEW QUESTION 20
The data on the affected system must be backed up so that it can be retrieved if it is damaged during incident response. The system backup can also be used for further investigations of the incident. Identify the stage of the incident response and handling process in which complete backup of the infected system is carried out?
- A. Containment
- B. Eradication
- C. Incident recording
- D. Incident investigation
Answer: A
NEW QUESTION 21
A self-replicating malicious code that does not alter files but resides in active memory and duplicates itself, spreads through the infected network automatically and takes advantage of file or information transport features on the system to travel independently is called:
- A. Trojan
- B. Worm
- C. Virus
- D. RootKit
Answer: B
NEW QUESTION 22
The process of rebuilding and restoring the computer systems affected by an incident to normal operational stage including all the processes, policies and tools is known as:
- A. Incident Management
- B. Incident Response
- C. Incident Recovery
- D. Incident Handling
Answer: C
NEW QUESTION 23
......
100% Valid and Newest Version 212-89 Questions & Answers shared by Exambible, Get Full Dumps HERE: https://www.exambible.com/212-89-exam/ (New 163 Q&As)