Our pass rate is high to 98.9% and the similarity percentage between our 200-201 study guide and real exam is 90% based on our seven-year educating experience. Do you want achievements in the Cisco 200-201 exam in just one try? I am currently studying for the Cisco 200-201 exam. Latest Cisco 200-201 Test exam practice questions and answers, Try Cisco 200-201 Brain Dumps First.
Online 200-201 free questions and answers of New Version:
NEW QUESTION 1
A security engineer deploys an enterprise-wide host/endpoint technology for all of the company's corporate PCs. Management requests the engineer to block a selected set of applications on all PCs.
Which technology should be used to accomplish this task?
- A. application whitelisting/blacklisting
- B. network NGFW
- C. host-based IDS
- D. antivirus/antispyware software
Answer: A
NEW QUESTION 2
What specific type of analysis is assigning values to the scenario to see expected outcomes?
- A. deterministic
- B. exploratory
- C. probabilistic
- D. descriptive
Answer: A
NEW QUESTION 3
What is the difference between statistical detection and rule-based detection models?
- A. Rule-based detection involves the collection of data in relation to the behavior of legitimate users over a period of time
- B. Statistical detection defines legitimate data of users over a period of time and rule-based detection defines it on an IF/THEN basis
- C. Statistical detection involves the evaluation of an object on its intended actions before it executes that behavior
- D. Rule-based detection defines legitimate data of users over a period of time and statistical detection defines it on an IF/THEN basis
Answer: B
NEW QUESTION 4
Drag and drop the technology on the left onto the data type the technology provides on the right.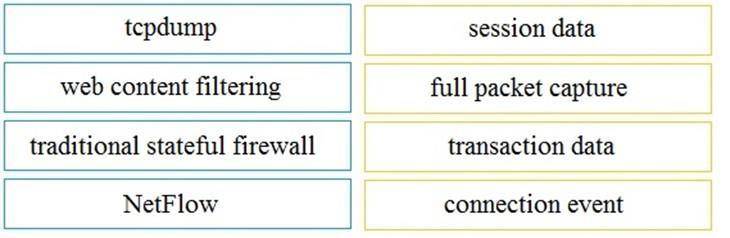
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 
NEW QUESTION 5
Which two elements are used for profiling a network? (Choose two.)
- A. session duration
- B. total throughput
- C. running processes
- D. listening ports
- E. OS fingerprint
Answer: DE
NEW QUESTION 6
Which security technology allows only a set of pre-approved applications to run on a system?
- A. application-level blacklisting
- B. host-based IPS
- C. application-level whitelisting
- D. antivirus
Answer: C
NEW QUESTION 7
What causes events on a Windows system to show Event Code 4625 in the log messages?
- A. The system detected an XSS attack
- B. Someone is trying a brute force attack on the network
- C. Another device is gaining root access to the system
- D. A privileged user successfully logged into the system
Answer: B
NEW QUESTION 8
How does an SSL certificate impact security between the client and the server?
- A. by enabling an authenticated channel between the client and the server
- B. by creating an integrated channel between the client and the server
- C. by enabling an authorized channel between the client and the server
- D. by creating an encrypted channel between the client and the server
Answer: D
NEW QUESTION 9
Which utility blocks a host portscan?
- A. HIDS
- B. sandboxing
- C. host-based firewall
- D. antimalware
Answer: C
NEW QUESTION 10
A system administrator is ensuring that specific registry information is accurate.
Which type of configuration information does the HKEY_LOCAL_MACHINE hive contain?
- A. file extension associations
- B. hardware, software, and security settings for the system
- C. currently logged in users, including folders and control panel settings
- D. all users on the system, including visual settings
Answer: B
NEW QUESTION 11
What is a benefit of agent-based protection when compared to agentless protection?
- A. It lowers maintenance costs
- B. It provides a centralized platform
- C. It collects and detects all traffic locally
- D. It manages numerous devices simultaneously
Answer: B
NEW QUESTION 12
What is the difference between the ACK flag and the RST flag in the NetFlow log session?
- A. The RST flag confirms the beginning of the TCP connection, and the ACK flag responds when the data for the payload is complete
- B. The ACK flag confirms the beginning of the TCP connection, and the RST flag responds when the data for the payload is complete
- C. The RST flag confirms the receipt of the prior segment, and the ACK flag allows for the spontaneous termination of a connection
- D. The ACK flag confirms the receipt of the prior segment, and the RST flag allows for the spontaneous termination of a connection
Answer: D
NEW QUESTION 13
Refer to the exhibit.
In which Linux log file is this output found?
- A. /var/log/authorization.log
- B. /var/log/dmesg
- C. var/log/var.log
- D. /var/log/auth.log
Answer: D
NEW QUESTION 14
An organization has recently adjusted its security stance in response to online threats made by a known hacktivist group.
What is the initial event called in the NIST SP800-61?
- A. online assault
- B. precursor
- C. trigger
- D. instigator
Answer: B
NEW QUESTION 15
Which two elements are assets in the role of attribution in an investigation? (Choose two.)
- A. context
- B. session
- C. laptop
- D. firewall logs
- E. threat actor
Answer: AE
NEW QUESTION 16
An engineer runs a suspicious file in a sandbox analysis tool to see the outcome. The analysis report shows that outbound callouts were made post infection.
Which two pieces of information from the analysis report are needed to investigate the callouts? (Choose two.)
- A. signatures
- B. host IP addresses
- C. file size
- D. dropped files
- E. domain names
Answer: BE
NEW QUESTION 17
......
P.S. Easily pass 200-201 Exam with 98 Q&As Allfreedumps.com Dumps & pdf Version, Welcome to Download the Newest Allfreedumps.com 200-201 Dumps: https://www.allfreedumps.com/200-201-dumps.html (98 New Questions)