Want to know Examcollection 1D0-61C Exam practice test features? Want to lear more about CIW CIW Network Technology Associate certification experience? Study 100% Guarantee CIW 1D0-61C answers to Far out 1D0-61C questions at Examcollection. Gat a success with an absolute guarantee to pass CIW 1D0-61C (CIW Network Technology Associate) test on your first attempt.
Free 1D0-61C Demo Online For CIW Certifitcation:
NEW QUESTION 1
Henry is the network manager at XYY Corporation, a large manufacturing company that competes in the global market. The company’s computing environment is extremely complex and includes several proprietary software systems, all of which require custom configuration of network devices to operate correctly. The company’s executive management team believes that they can benefit by switching the company over to any cloud-based service. Henry disagrees.
What is a disadvantage of cloud-based services that Henry can cite to support his position?
- A. Cloud-based services provide no maintenance or support.
- B. Cloud-based services are typically more costly than in-house solutions.
- C. The company must typically purchase additional servers to support connections to these types of cloud-based service providers.
- D. Cloud-based services are typically more limited in offerings and configurations than the company currently supports in-house.
Answer: D
NEW QUESTION 2
You want to restrict host access to a wireless access point. What is the best way to do this?
- A. Enable MAC address filtering at each host.
- B. Log in to the access point and configure features, such as changing the SSID.
- C. Change the Direct Sequence Spread Spectrum (DSSS) signal at both the access point and each hosts NIC.
- D. Install software on the host you want to limit, then use a Web browser to log in to the host and configure it with the necessary settings to use the access point.
Answer: B
NEW QUESTION 3
The Windows Device Manager is a tool that enables you to perform a variety of tasks, including:
- A. Map to a printer.
- B. Ping anIPaddress.
- C. Defragment a hard drive.
- D. Change a resource assignment.
Answer: D
NEW QUESTION 4
Which of the following is a drawback to using Wired Equivalent Privacy (WEP)?
- A. Wireless network overhead is excessive.
- B. Symmetric-key encryption is susceptible to cracking.
- C. The number of devices that can communicate using WEP is limited.
- D. Encryption and decryption speeds are slower compared to other protocols.
Answer: B
NEW QUESTION 5
Which security issue is most closely associated with wireless networks?
- A. Spoofing
- B. Wardriving
- C. Eavesdropping
- D. Man-in-the-middle
Answer: B
NEW QUESTION 6
The Internet has enabled many new anti-social activities, such as online stalking, cyberbullying, and addiction to solitary online activities. Which choice is the most feasible way for schools and parents to reduce cyberbullying?
- A. Monitor, track and record all online activity conducted by students.
- B. Teach teens that the use of online communication is a freedom of expression.
- C. Prevent students from accessing the Internet while at school so that they learn good habits.
- D. Educate students about cyber-ethics and the consequences of questionable online behavior.
Answer: D
NEW QUESTION 7
Three hardware devices need to communicate with the CPU simultaneously. Which of the following will each device need to issue?
- A. DMA request
- B. CON request
- C. Interrupt request (IRQ)
- D. Input/output request (I/O)
Answer: C
NEW QUESTION 8
Cloud-computing enables mobile devices to provide users with access to a wide variety of applications and services. Which of the following is a disadvantage of mobile devices?
- A. Mobile devices cannot accommodate Web browsing.
- B. Mobile devices cannot easily be used for checking e-mail.
- C. Mobile devices cannot access software hosted on remote servers.
- D. Mobile devices cannot accommodate large database installations or applications.
Answer: D
NEW QUESTION 9
Configuring a wireless network involves several steps. Which of the following is a task that should be performed to configure and connect to a wireless network?
- A. Configure a certificate authority and configure the trust settings.
- B. Configure the wireless AP’s SSID, encryption level and shared key.
- C. Connect your computer to the same network hub as the wireless AP.
- D. Connect your computer to the same network switch as the wireless AP.
Answer: B
NEW QUESTION 10
What is the biggest security concern with wireless networks?
- A. Firewall software is not available for access points.
- B. Wireless encryption algorithms must be implemented.
- C. Wireless networks do not support intrusion detection.
- D. Wireless networks do not support encryption via an access point.
Answer: B
NEW QUESTION 11
When comparing IPv4 to IPv6, which of the following is an advantage of the IPv6 network addressing scheme?
- A. Larger address space
- B. Shorter address space
- C. High dependence on network routers
- D. Fast and unencrypted network transmissions
Answer: A
NEW QUESTION 12
Consider the network configuration shown in the command prompt: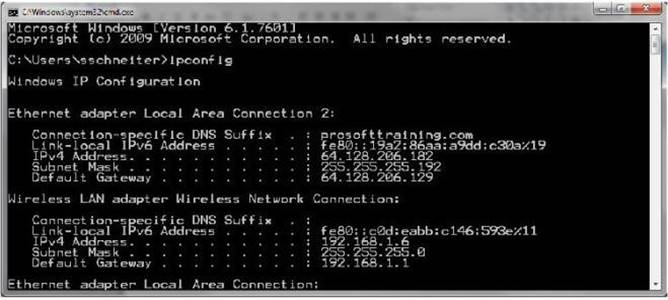
What does the Default Gateway identify?
- A. The file server on the network
- B. The local host on the network
- C. The computer on the network
- D. The router on the network
Answer: D
NEW QUESTION 13
Sally is a network technician at Acme Corporation. She has been directed to configure the network adapter for a company laptop so that it can be used to connect to the company network and the Internet. What is one of the required TCP/IP settings that she will need to configure?
- A. MAC address
- B. Default gateway
- C. Workstation name
- D. Loopback address
Answer: B
NEW QUESTION 14
You are distributing a large video game file using BitTorrent. First, you upload the initial file and make it available via a central server called a tracker. Other users can then connect to the tracker and download the file. Each user who downloads the file makesit available to other users todownload. The use of BitTorrent significantly reduces the original provider’s hardware and bandwidth resource costs. BitTorrent is an example of what type of network?
- A. Centralized network
- B. Client-server network
- C. Peer-to-peer (P2P) network
- D. Virtual private network (VPN)
Answer: C
NEW QUESTION 15
Which of the following is generally a component of a BYOD policy?
- A. Scope of control
- B. Insurance on devices
- C. Maintenance provision
- D. Device replacement or upgrade
Answer: A
NEW QUESTION 16
What is the distinguishing difference between a LAN and WAN?
- A. A LAN is a group of networked computers within a confined geographic area.
- B. A WAN is a group of networked computers within a confined geographic area.
- C. A LAN typically provides slower network connection speeds than a WAN.
- D. A WAN is commonly used for intra-office communication.
Answer: A
NEW QUESTION 17
Disaster recovery planning is considered a best practice for all organizations. It is even more important when cloud-computing services are used. Which of the following should be included as part of a disaster recovery plan for companies that use cloud-based services?
- A. Company organizational chart
- B. Malware and anti-virus software updates
- C. Service-level agreement with a cloud-provider
- D. Inventory of services not dependent on the cloud provider
Answer: C
NEW QUESTION 18
Jose is experiencing performance problems with his notebook computer that he purchased a year ago. Upon discussing this issue with him, you learn that he has never deleted any temporary files since owning the device. What can Jose do to fix this problem most efficiently?
- A. Reformat his hard drive.
- B. Use the Windows chkdsk utility.
- C. Use the Windows Disk Cleanup utility.
- D. Back up his computer and delete the active partition.
Answer: C
NEW QUESTION 19
Acme Corp. is a small manufacturing company. To reduceIT infrastructure costs, it uses cloud- based services extensively and strives to have the least amount ofIT equipment onsite. Last year, Acme suffered a failure that resulted in significant down time and data loss. Management has decided to implement a continuous data protection (CDP) solution. Which type of CDP solution best fits Acme’s situation?
- A. Cloud-only solution
- B. Local systems solution
- C. Distributed network services provider
- D. Contracted network services provider
Answer: A
NEW QUESTION 20
Selena has run out of memory on her phone’s SD card. She has decided to store the files she has accumulated on a third-party cloud service provider’s drives. Which of the following is a typical issue that she may encounter?
- A. The files become corrupted due to an attack from a hacker botnet.
- B. The files become unavailable whenever Internet connectivity is lost.
- C. The files become unavailable because they are being shared with other users.
- D. The files become corrupted because the provider uses a proprietary compression algorithm during transit.
Answer: B
NEW QUESTION 21
Wireless networks are subject to more security issues than standard wired networks. Which wireless security protocol can prevent unauthorized devices from connecting to the wireless network?
- A. WPA2
- B. RSA
- C. AES
- D. DES
Answer: A
NEW QUESTION 22
What should be your first step when troubleshooting a network connection that uses a cable modem?
- A. Ping the proxy server.
- B. Ping the default gateway.
- C. Ping local devices using their DNS names.
- D. Ping local devices using their IP addresses.
Answer: D
NEW QUESTION 23
Your company is investigating the possibility of moving its customer service management system to a cloud service provider. The sales rep for the cloud service provider has presented many advantages that would benefit your company. What would be a potential drawback of moving the CRM from your current in-house solution?
- A. If your company’s Internet service is interrupted for any reason at any time, you will not have access to the CRM.
- B. More company employees will have access to the system, which could result in unauthorized access to confidential data
- C. Special equipment will need to be purchased and maintained in your office in order to access and maintain the CRM once it is migrated to the hosted cloud service.
- D. Migrating the CRM to the cloud service provider will eliminate several jobs in your customer service department because their job roles will no longer be required.
Answer: A
NEW QUESTION 24
Which term describes a compact personal computer that relies on a touch screen forinput, generally uses a solid-state drive instead of a traditional hard disk, and relies on wireless or mobile networks for connectivity?
- A. Tablet
- B. Laptop
- C. Netbook
- D. Portable media player
Answer: A
NEW QUESTION 25
......
100% Valid and Newest Version 1D0-61C Questions & Answers shared by Surepassexam, Get Full Dumps HERE: https://www.surepassexam.com/1D0-61C-exam-dumps.html (New 59 Q&As)